Securing IT Infrastructure: The Plugable Advantage in Wired Connectivity
Bernie Thompson | March 23, 2024
Plugable Technologies, a leader in workplace productivity through its innovative USB connectivity solutions, was founded by Bernie Thompson, a veteran of Microsoft and IBM. It champions wired connectivity over wireless to boost security significantly, mitigating risks associated with wireless exploits by offering point-to-point data transmission options. This security-first approach, emphasizing software-free hardware, ensures a minimized security risk, which is paramount in today's vulnerable digital landscape.
Products like the Plugable USB Data Blocker (USB-MC1) and the Google Works With Chromebook certified docking station (UD-MSTHDC) exemplify the commitment to deliver secure, efficient, and reliable connectivity solutions.
Security Focus of Plugable Products
Wired Over Wireless: Enhanced Security and Control. Choosing wired solutions like those offered by Plugable significantly enhances security over wireless alternatives. For instance, wireless networks are susceptible to various exploits such as 'Evil Twin' attacks, where malicious Wi-Fi access points mimic legitimate ones to capture sensitive data. There's also the risk of 'Man-in-the-Middle' attacks, intercepting and altering data in transit over wireless connections. By contrast, Plugable’s point-to-point wired connectivity options greatly reduce these risks, offering a more secure data transmission channel and allowing for enhanced physical control, crucial in high-security environments.
Software-Free Hardware: Minimizing Vulnerabilities. Plugable’s strategy of offering hardware that operates independently of third-party software significantly reduces security risks. For example, in Windows systems, third-party software installations have led to breaches like the SolarWinds hack, where malicious code was inserted into software updates, compromising thousands of users. On Mac systems, instances like the Zoom vulnerability exposed users to potential camera hijacking due to third-party software weaknesses. By eliminating the need for such software for the majority of Plugable’s product line, Plugable's hardware solutions inherently minimize these vulnerabilities, offering a safer and more reliable IT infrastructure for businesses and governments.
Reliance on Built-In USB Class Drivers: Ensuring Compatibility and Security. Plugable's commitment to utilizing built-in operating system USB class drivers ensures only trusted drivers are run, along with immediate system compatibility while leveraging of security updates provided by operating system vendors. Plugable avoids third-party drivers where possible. And when they are required, Plugable’s devices can use Microsoft-approved drivers delivered by Windows Update. Plugable’s focus on the security and reliability of its products is a crucial factor for government and enterprise users.
Secure and Non-Volatile Firmware: Maintaining Data Integrity. Plugable offers a spectrum of firmware options across its product range, catering to diverse security needs. This includes devices with non-volatile firmware, ensuring that the device itself cannot be hacked, and devices with secure update mechanisms for firmware, safeguarding against unauthorized modifications. For example, Plugable’s Works with Chromebook™ dock is securely updated by Google as part of the Chromebook’s own automatic updates. Plugable is able to provide volatility statements for any of our products, detailing the firmware and other writable features which relate to security.
USB as a Safe Data Transfer Mechanism. When transferring data between systems, Plugable's point-to-point USB-based solutions offer a distinct advantage over network transfers, or more vulnerable internet-dependent services like Microsoft OneDrive or physical hard drives. While cloud services like OneDrive transmit data across the internet, potentially exposing it to cyber threats during transit, Plugable’s USB products enable direct, local data transfer between devices, significantly reducing the risk of interception or unauthorized access. Similarly, compared to external hard drives, which can pose data leakage risks if stolen or improperly disposed of, USB connections offer a more secure and controlled environment for data transfer, ensuring that sensitive information remains confined to the user's immediate devices. This direct and localized approach to data transfer underscores Plugable’s emphasis on robust security in data handling.
Thunderbolt Certification: Ensuring Security Through Stringent Oversight. Thunderbolt certification, controlled by Intel and Apple—both US-based companies—demands that Thunderbolt devices like those from Plugable adhere to common standards for connectivity, power delivery, and security. A crucial aspect of this certification process is that any design changes to Thunderbolt functionality, including to firmware, require recertification. This ensures that any modifications maintain the stringent security standards initially met. Thunderbolt firmware, controlled by Intel and Apple, further mitigates the risk of unauthorized or malicious alterations that could compromise the device's security integrity.
American Ownership: Adherence to Stringent Security Standards. As an American-owned and operated entity, Plugable is deeply committed to adhering to the stringent security and compliance standards set by the United States. This adherence instills a robust level of trust and reliability among enterprise and government buyers, ensuring that the products they use meet the high expectations of U.S. regulatory requirements, crucial for sensitive and secure operations.
Manufacturing Diversity: Strengthening Supply Chain Security. In addition to its American roots, Plugable distinguishes itself by diversifying its manufacturing base beyond China. This strategic approach to manufacturing ensures a more secure and transparent supply chain. By distributing production across various geographic locations, including Thailand and Taiwan, Plugable provides an additional layer of security and resilience, essential in the current global market where supply chain integrity is of paramount importance, especially for sensitive government and enterprise applications.

Product Security Highlights
Plugable’s USB Data Blocker (USB-MC1)
The Plugable USB-MC1 adapter enhances device security and charging efficiency in multiple ways. By converting any USB data port into a charge-only port, it acts as a data blocker, safeguarding the device and its data from potential hackers and viruses commonly associated with "juice jacking" – a method where malicious entities might use public charging stations to compromise devices. This feature is particularly beneficial in preventing unauthorized data transfer and access, offering users peace of mind when charging their devices in public spaces like airports, coffee shops, and libraries. The FCC and FBI have warned about the potential dangers of Juice Jacking, and the inexpensive Plugable USB-MC1 provides 100% protection from this type of attack. Furthermore, the adapter facilitates faster charging by allowing devices to draw power at 1A or more, doubling the charging speed compared to the standard 500mA provided by most computer USB ports. This can significantly reduce charging time and even enable charging on powered USB hubs without a connected computer. Its compact, travel-ready design makes it an ideal accessory for secure and efficient charging on the go.

Plugable’s Google Works With Chromebook Docking Station (UD-MSTHDC)
Plugable’s Works With Chromebook-certified dock is designed specifically for the Chrome OS “Zero Trust” ecosystem, ensuring seamless integration and compatibility. This docking station adheres to strict security guidelines set by Google, including encrypted, secure firmware to protect against unauthorized access. When paired with a Chromebook, the docking station receives seamless, cryptographically authenticated updates from Google, including the latest security patches, directly to the dock, reducing the risk of potential breaches. This, combined with Plugable's commitment to reliability and lifetime support from their Redmond, Washington-based team, makes the Plugable UD-MSTHDC an effective tool for enhancing desktop security. This product is Made in Thailand with a supply chain controlled by USA and Taiwanese-based partners.

Secure Thunderbolt speed point-to-point data transfer with Plugable (TBT-TRAN)
Secure, high-speed 10 Gbps data transfer using a Thunderbolt cable, such as the one provided by the Plugable TBT-TRAN, offers significant advantages over traditional data transfer methods, especially when compared to transfers over the Internet, a network, or wireless methods. Thunderbolt technology delivers unparalleled data transfer speeds, enabling large files and datasets to be moved in a fraction of the time it would take using conventional methods. For instance, transferring a 20GB file over a standard home internet connection could take hours, depending on the speed and congestion of the network, while the same transfer could be completed in a matter of seconds using a Thunderbolt connection. Additionally, Thunderbolt cables provide a direct, point-to-point connection, greatly reducing the risk of data interception or eavesdropping that is inherent to wireless and networked communications. This direct connection also bypasses the need for data to travel over potentially insecure or unreliable networks, further enhancing both the security and reliability of data transfers. For support of older USB-A PCs and the secure transfer of Windows account data from old to new PCs without exposing the data to the cloud, see the Plugable USB3-TRAN.
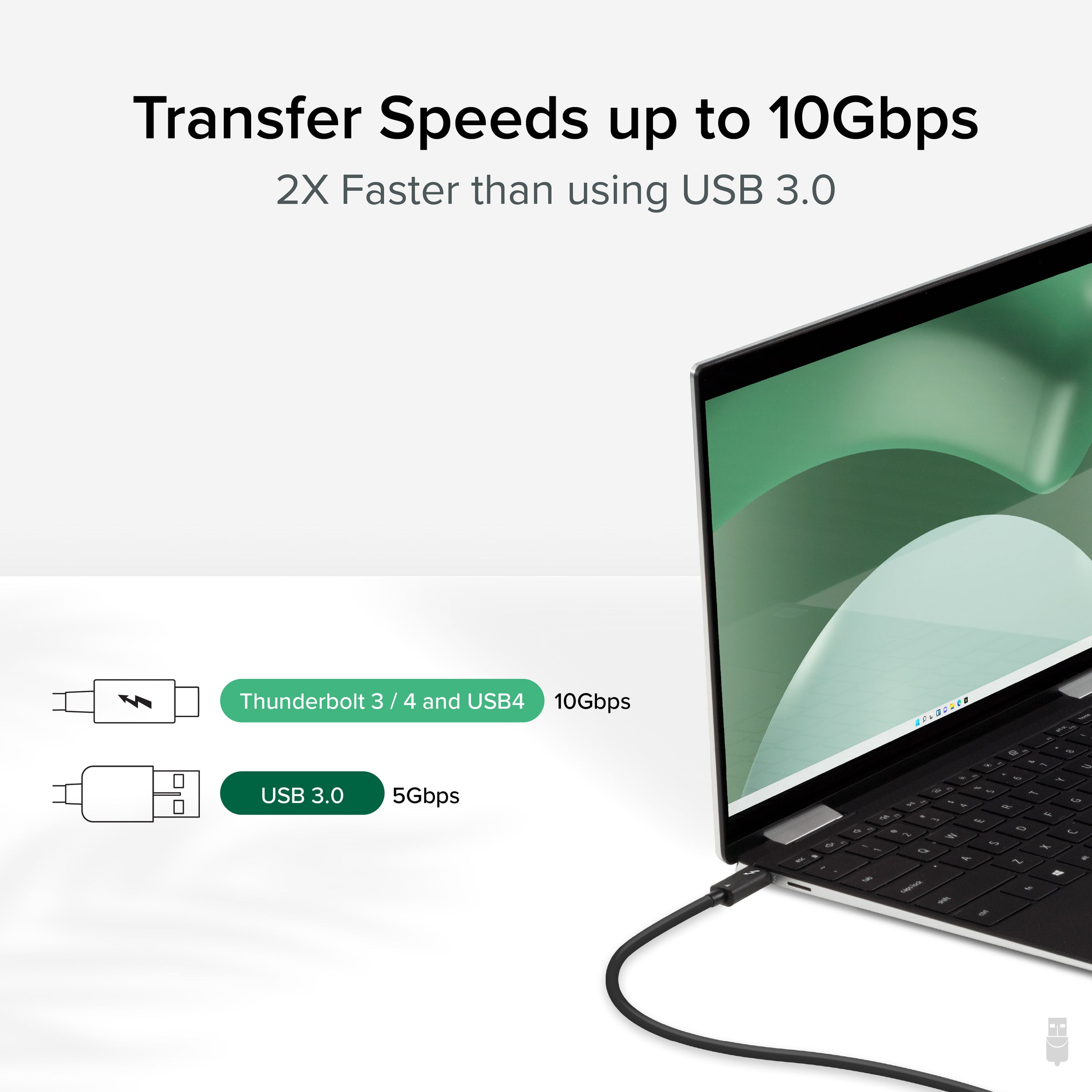
The Plugable TBT-TRAN enhances these benefits by not only providing a Thunderbolt Certified cable capable of these high-speed transfers but also by bundling it with American-made Bravura transfer and sync software. This software adds an additional layer of functionality and security, allowing for seamless data transfers and syncs between devices. The combination of Thunderbolt's high-speed capabilities and Bravura's secure software solution contrasts sharply with the latency and security vulnerabilities associated with internet or network-based transfers, including those conducted over Wi-Fi. Wireless transfers, while convenient, are susceptible to interference and significantly slower speeds, not to mention the increased risk of unauthorized access or data leakage. By using the Plugable TBT-TRAN with its certified Thunderbolt cable and Bravura software, users can achieve not only lightning-fast data transfers but also a level of security and reliability that is virtually impossible to match with traditional network or wireless data transfer methods.
All products are backed by a 2-year warranty and support, emphasizing Plugable's commitment to quality, performance, and customer satisfaction. These solutions are designed to meet the diverse needs of users looking to expand their device's connectivity, charge efficiently, or enhance their multimedia and work setups.
Return to TopView Other Articles in Category
Related Articles
- Enterprise Guide: How Many External Monitors Can a Laptop Really Support?
- The Enterprise Guide to Choosing the Right Docking Technology for Multi-Display Setups
- At CES, Plugable Introduces Its Flagship Thunderbolt 5 Dock Of 2026
- Plugable Introduces TBT5-AI at CES: Secure, Local AI Powered by Thunderbolt 5
- Head-to-Head: Plugable UD-7400PD vs. Anker Prime 14-in-1


Loading Comments